Infographic brought to you by Wrike project management online tools
Startup Launch Checklist: 22 Steps to Success
How Working Memory Allows You To Take Control Over Your Own Thoughts
One of the things that put us, as humans, at the top of the food chain is the fact that we’ve evolved substantially enough to be able to take control of our own thoughts. But, the big question is, how do we do it?
To try and answer that age-old question, MIT neuroscientist Earl Miller along with co-authors Mikael Lundqvist and Andre Bastos presented a new working memory model in the 30th-anniversary edition of Neuron that explains all about how the brain holds information and how it has control over that information.
The way in which the brain operates its working memory is depicted in the model. It shows how waves in the low alpha and beta frequencies contain our goals and knowledge as well as helping to regulate the higher frequency gamma rays. In addition to that, it shows how the temporary storage of that information is achieved through the help of synapses.
There are two fundamental beliefs challenged by the model. The first is that brainwaves don’t have any functional meaning and are simply byproducts of brain activity. The second is that the working memory is made up of a constant hum of neural firing, opposed to short, sharp bursts. But the newer model shows otherwise.
Firstly, it shows what effect different wave frequencies have on brain function. During the study, the animals were trained to play a game to show how well they recognized patterns. They were all shown a series of images and had to try and judge the sequence of the next two images.
Upon recording brain activity, the researchers found a distinct pattern of interplay between the beta and gamma wave frequencies. In this instance, beta levels increased when taking in information or reading it out, while gamma levels declined when this information was no longer needed. More amazingly, the researchers saw how deviations from these patterns strongly corresponded to the animals making mistakes. “This adds to the mounting evidence that brain waves have a major functional role in the brain,” says Miller.
The paper provides a good foundation in which for other researchers to follow when studying working memory. “While many aspects of this theory need to be linked more closely to behavior, Miller’s account provided a roadmap for the future of the working memory field,” says Sabine Kastner, professor of psychology and neuroscience at Princeton University. The next move for Miller and the team is to explore more deeply the finer points of working memory and to try and find ways to enhance it when it comes to those suffering from psychiatric diseases.
Image; DepositPhotos
Benefits of Automation in IT Infrastructure
The convergence of technology in this digital age is phenomenal. At the core, every organization is looking forward to a single speedy solution that provides them with the opportunity to streamline their operational efficiency and cut costs of IT functionalities. From the release of application to customer support, every aspect of the enterprise needs faster solutions. The competitive distinctness, customer loyalty, and good business outcomes are all dependent on the acceleration of business processes.
While the legacy IT infrastructure is still essential, it has become more of a utility. Enterprises today need an agile, flexible and quickly scalable technology foundation to drive business, which has pushed it to the back seat. Companies with traditional technology architectures, therefore, face a predicament: on how to strike a balance between the present and required state of IT infrastructure. To achieve this balance, the first step should be to discard is IT’s an obsession with legacy systems. And the second would be to adopt – IT Infrastructure Automation.
A business can only move as fast as its IT infrastructure. Automation accelerates the complete business process, not just the IT infrastructure. With automation, enterprises can explore and take advantage of various opportunities. Such as:
- Adoption of DevOps
DevOps is the path towards the agility that organizations require for releasing better quality products. The adoption of DevOps and its integration in the functionalities require infrastructure automation. Research by Forrester suggests that enterprises have achieved only 20% of the benefits of automation as its implementation is limited. Proper functioning of DevOps requires full infrastructure automation throughout the lifecycle of the process.
- Self-Service Portals and Better User Experience
The benefits of service catalog are expanding beyond IT processes to various areas of businesses. From supplier management (contract renewal management, bid review) to HR (joining, benefits, and compensation), it can benefit many other parts of a business as well. These catalogs accelerate business productivity, and automation accelerates service delivery. For full utilization of self-service portals, companies need to move towards business process automation. Automating every repeatable workflow in the process provides the full business value of self-service portals.
- Maximum Utilization of Cloud
Even as most of the organizations are utilizing cloud infrastructure, there are many untapped benefits in the cloud that can provide value to businesses. Smart infrastructure automation provides methods for making the best use of various cloud opportunities at a faster rate. Automation also provides more control of cloud activities by dividing the workload and then allocating it amongst different clouds (private/hybrid/public).
- Programmable Infrastructure
The importance and standard of data centres are changing rapidly across organizations. The data centres today are everywhere due to the availability of cloud storage. They can also be on a hosted site, various social storage platforms, or at any service providers facility. The ability to orchestrate and automate infrastructure facilities provides enterprises with high-level data security. Automation allows programming storage as a service through hosted sites, secondary data centres, social platforms, and public clouds.
- Bi-modal IT
IT has always been a strategic and innovative partner of the business process. While continuing to fulfill the service level agreements, IT also provides better security controls, reduces costs and maintains operational capabilities. Bi-modal IT, which is the management of two separate modes of IT delivery – one focused on stability and other on agility, is a sustainable solution for businesses in the advancing digital world. Automation acts as a catalyst for transitioning the traditional IT methods to bi-modal IT. Furthermore, automation can accelerate IT processes and provide stability through cost savings.
- Reducing Costs
IT infrastructure automation is also the primary factor in reducing the costs of delivering excellent quality services and improving the user experience. Automation helps in removing defects and outages; thus, enabling IT to optimize the resource capacity better. It also allows control of labor allocation and utilization across the entire business process.
IT infrastructure automation is the key to both cost-optimization of traditional IT and digital transformation. Enterprises can achieve higher productivity with greater efficiency by increasing their business agility through automation. Cut in labor costs, optimization of resources, improved user experience and adoption of DevOps are only some benefits that automation has in store. The unexplored opportunities of the future are no longer a dilemma because of automation.
Image; DepositPhotos
How do Men deal with Infidelity in a Marriage?
Do you want to cheating wife’s text messages?
In 40% infidelity cases, men are cheated upon by their wives.
So in some marriages, the relationship need help, in some of the cases, both parties aware of their affair, but they cannot address the issue. In others time, the partner sees the infidelity and try to find some ways to end the relationship.
Nonetheless, of knowing the underlying reason, why a spouse cheats, it can either devastating the marriage or be the catalyst for rebuilding the marriage relationship. It’s imperative that you remain calm during this whole event. Don’t say anything or you will regret it later.
How to Deal with the Issue at Hand?
It depends on how the matter of the infidelity deals with. The husband and wife need a serious commitment to saving their marriage. It needs to decide to move for further damage.
Whether the underlying the cause is concerned, it causes the real damage to the relationship. At some extent, the partner feels the stonewalled or feels demeaned or abused and starts questioning about his self-worth.
It creates frustration, and regrettable things are said the experts suggest that infidelity is the key indicator of the divorce. If needed, try tracking her with Cocospy Mobile Tracker App for Free.
Understanding someone’s Perspective
Cheated on husband can escalate every situation. The relationship does not become successful in communication and cooperation.
The couple therapy is also designed to solve the problems of the couples and understands why the distances are taking place or identify the behavior and try to correct it. Here are some tips and tricks that help to sustain the congenial relationship.
What to Do Next?
The couple must adopt a structural approach of communication: which may include the number of factors:
- The husband must be aware of the body language of the partner.
- The usage of the right words help to pave the new path of the understanding
- Never choose a work neither establishing bitter relationship nor accusing your partner of cheating.
- The partner must agree on the topic or postpone the conversation, When the things are continuous on agree conversation, so the things are smoothly settling down.
- The partner accepts the feedback and acknowledges, so the discussion chooses the right track to resolve the issues.
- The husband must find a safe place for the discussion, where the spouse does not feel guilty.
- The couple must express the understanding of the situation
It takes time to get used to these techniques and tips. Eventually, it creates the understanding and resolves the matter rather than react against it.
Fighting the War
Are you worried your spouse might be cheating on you? All the mobile record can easily be tracked and maintains the real activities in details. The coco spy is a trusted solution of your problem. Coco spy is a powerful android for the cheating spouse.
The husband can easily spy on wife mobile phone without touching her cell. In the era of technology, it is the desire of the man that woman must be loyal to him. Because of the external influence, the women come at stake.
The man wants to save his identity and integrity. To know about the woman fidelity, the man uses different trick and methods to check the loyalty of woman. These tricks provide help to know to what extent spouse is honest with the husband.
A Solution
 A Tracker App lets you track, receive and send messages. Cocospy tracker is a user-friendly and comes with the advanced features of spying. The person can track all sent and receive messages along with the name and number and easily get the time and date stamp. Coco spy is compatible with IOS and Android.
A Tracker App lets you track, receive and send messages. Cocospy tracker is a user-friendly and comes with the advanced features of spying. The person can track all sent and receive messages along with the name and number and easily get the time and date stamp. Coco spy is compatible with IOS and Android.
The high technology helps to monitor her. That’s why, it is the safest way to find out the clue about your wife, don’t wait, until, it becomes too late, a lot of damage has been done. By using this technology, try to find out the real cause of the disloyalty and try to solve out the matter at the initial level.
Image; DepositPhotos
The Trouble With Growing Your Own DDoS Protection Methods
If you’re keeping up with what’s happening in the wonderful world of IT, you’re probably reading the blood-curdling headlines about 1.7 Tbps distributed denial of service (DDoS) attacks and gut-wrenching descriptions of average $40,000-per-hour costs of unmitigated attacks.
You’ve also probably digested the fact that no business is too large or too small to be a target of distributed denial of service attacks. So, it’s natural to start thinking about IT security improvements. In these initial thoughts, it’s tempting to envisage a tidy, on-site operation. It has the latest hardware and software (you’re upgrading), and your IT team is in charge. But hold on a minute. Before you go any further, consider all your options before settling on a DIY security solution. There are many reasons why the wise choice is letting the security pros protect your network.
Five reasons to not DIY
The main reason to pass up DIY mitigation? Its limitations. Although tools and techniques of in-house DDoS mitigation are powerful, they can’t stop swift, massive, and sophisticated volumetric attacks. Remember, in on-premises DIY mitigation plans:
- Protection starts too late in the attack cycle. DIY protection methods are usually a reaction to the initial attack. By the time the IT security team starts working, much of the damage is done. This is especially relevant in DDoS attacks that include application-layer exploits.
- The ability to adjust configurations doesn’t always help. IT security pros can respond to an attack by adjusting configuration settings manually. However, this takes valuable time. Also, protection is good only for the same type of attack. This lack of flexibility becomes a problem in multi-vector exploits. When botmasters (human controllers of DDoS bots) change tactics in mid-attack, your protection loses its usefulness.
- Your network’s network bandwidth limits DIY protection efforts. Your DDoS protection is only as good as your bandwidth is large. DDoS attacks commonly measure many times more than the volume of enterprise network traffic.
- DIY protection can’t always distinguish malware and legitimate users. In-house, DDoS protection methods often involve static traffic rate limitations and IP blacklisting. When you use these relatively old-fashioned methods, legitimate users can be mistaken for malicious software. Being blocked from using your website is a quick way to lose customers.
- Prohibitive costs. For many companies wanting to upgrade their DDoS protection, this is the biggest problem of all. Purchasing, installing and deploying hardware appliances carry a hefty price tag that puts DIY protection beyond the budget of most organizations.
Don’t forget to protect your applications
Network users are discovering what IT security pros have known for a while. Volumetric attacks might be the familiar face of DDoS mayhem. In many cases, however, data and application security are also at risk.
That’s because DDoS attacks are often smokescreens to exploits that look for valuable data and information. In an application-layer DDoS attack, a botnet distracts the security team. While the security pros deal with the immediate problem, bots search for any information that can be sold on the Dark Web.
If you want to run your own DDoS protection methods, this is bad news. The security of applications that you run onsite is at risk. Given this expanded security scope, you would have to protect your apps by upgrading application-layer security measures. Experts recommend that to secure commercial applications, organizations must have their own remediation process, identity management methods, and infrastructure security procedures.
To run custom applications safely, you should adopt quite a few additional measures. These include application security testing, developer training, DevOps and DevSecOps practices, and maintaining an open source code inventory.
The ace up your sleeve—cloud-based mitigation services
The cloud is where you’ll find a powerful, cost-effective security option. Cloud-based, DDoS mitigation providers offer benefits that DIY methods lack.
- Broad DDoS protection. Cloud-based protection secures your infrastructure against attacks on your system’s network and application layers.
- No DDoS-related capital or operations costs. Mitigation service specialists offer DDoS protection as a managed service. There’s no need to invest in hardware or software. And, say good-bye to IT labor costs. Your IT staff doesn’t get involved in DDoS mitigation.
- No scalability problems. DDoS mitigation providers use large-scale infrastructures, with virtually unlimited bandwidth.
- No need to hire expensive talent. In-house DDoS protection solutions require IT pros with expensive, often hard-to-find knowledge and experience. The staffs of DDoS mitigation providers include the security and data specialists needed to keep DDoS attacks at bay.
- You spend less time and money. When you add up the costs of all required assets and resources, the conclusion is clear. You’ll spend far less time, effort, and budget when you engage off-premises, DDoS protection services.
These are the benefits that most DDoS mitigation services provide. However, advanced mitigation providers go several steps beyond this already high standard of performance. For example, automated defense methods built into DDoS response software eliminate the need for time-consuming human intervention. In fact, these capabilities reduce time to mitigation to mere seconds. (The current industry record is 10 seconds).
Isn’t it time to take advantage of this IT security firepower? With DDoS mitigation services at your back, you’ll never have to wince at another DDoS screamer headline again.
Image; DepositPhotos
It’s lights, camera, action with the 7 best movie tie-in slots
If you’re anything like us, you’re not content with just watching the action of your favourite films play out on the big screen. You want to get involved in the drama for yourself. That’s why movie tie-in slot games are so great. They give you the chance to play for big jackpot prizes alongside characters from cinema’s biggest and best blockbusters.
It doesn’t matter what genre of movies you’re into. You’ll find slots based on a huge selection of flicks, from gut-busting comedies like Ted and Mars Attacks!, to hard-hitting dramas like Platoon and Rocky.
And whatever movie tie-in slot choose, you’re in for a treat. Expect more stars on the reels than you’ll find on any red carpet, along with an iconic movie soundtrack and sometimes even actual footage from the film playing as you spin. This is in addition to all the cool things you’d expect from an ordinary online slot, like innovative bonus features, impressive graphics and (perhaps most importantly) huge cash prizes.
No doubt we’ve got you excited to try some movie-inspired slots for yourself right now. Check out our list of the 7 Best Movie Tie-In Slots according to the experts at bgo.com. All are available to play on your PC, smartphone or tablet.
I suppose all that’s left for us to say is have fun and we wish you the very best of luck.

Project Management Then & Now
Infographic brought to you by Wrike project portfolio management software
Why 2018 Was A Memorable Year For Esports
Esports has been growing rapidly for a while but 2018 was a truly special year for competitive gaming. Whether it was because of advances into mainstream society, enormous cash flow or huge events attracting thousands of fans, esports has grown a lot in the last twelve months. According to Statista, esports has attracted around 45 million more viewers in 2018, taking the total global figure to around 380 million. Let’s take a look at some of the reasons why this has happened.
It would be impossible to talk about the events of 2018 without discussing perhaps the largest competitive gaming event of all time – or at least the costliest. In August, the final tournament of the Dota Pro Circuit took place in Vancouver, Canada. The International 2018 saw 16 teams take part in a six-day double-elimination tournament to decide the winner. The prize pool for The International 2018 was a whopping $25 million in total.

The grand finals saw an all-acronym clash between PSG LGD and OG. Previously known as LGD Gaming, the Chinese side rebranded in April 2018 following an association deal with the French football club, Paris Saint-Germain. They had achieved considerable success in previous editions of the tournament, managing two top-four finishes in the last four editions of The International.
They were the clear favorites for the clash against the unfancied OG, a European side which had failed to reach the final eight in any previous International. They were the major underdogs but OG stepped up, triumphing 3-2 in the Grand Final to take home over $11 million in prize money. It was the single biggest win for a team in Esports history but it wasn’t the only historic competitive gaming moment in 2018.
The biggest tournaments in competitive gaming continued to wow. We had the first non-Korean winner of the Starcraft 2 World Championships while Counter Strike’s major tournaments, FACEIT Major: London and ELEAGUE Major: Boston were won by Astralis and C9 respectively. It was certainly a memorable year for Cloud9, they achieved major victories in almost every game they had a team involved in including Rocket League, League of Legends, Rainbow Six: Siege, and PlayerUnknown’s Battlegrounds.
2018 also saw the inaugural season of The Overwatch League, Blizzard’s competitive tournament for the popular first-person shooter. There was a considerable amount of scepticism about the league prior to launch with fans and experts alike seemingly unconvinced by its feasibility and city-based team structure. Activision Blizzard invested huge sums of money in the league and fortunately for them, their gamble paid off in season 1.

OWL was a big hit with fans, with viewing numbers regularly reaching six-figures across all platforms. Similarly, when the Season 1 Grand Finals came around, OWL had to be moved across America to the 11,000-seater Barclays Centre in New York City in order to accommodate the in-person demand. The London Spitfire eventually triumphed, beating Philadelphia Fusion 2-0 in the Grand Finals to take home the $1,000,000 grand prize.
If the Overwatch League was popular with fans, it was even more so with sponsors. Some huge companies got in on the action with Blizzard signing deals with Omen by Hp, T-M, bile and Intel to their list of official partners. The league also signed a multi-million dollar deal with Twitch and the finals were even broadcast on ESPN.
Sponsorship is certainly on the up in esports and 2018 was another landmark year for leagues, teams and players alike. Universal Music agreed on a deal with Luminosity Gaming, Online Bookmaker Betway extended its partnership with the team Ninjas in Pyjamas, and McDonald’s even cancelled its sponsorship deal with the German Football Federation in favour of a contract with ESL. Indeed, Statista estimates that esports sponsorship could treble between 2016 and 2020, reaching an estimated figure of around $1.2 billion. This sort of investment is vital in the continued growth of competitive gaming and 2018 has been one of the best years on record for sponsorship deals.
It has been a truly memorable year for Esports. From new major tournaments to the largest prize pool in competitive gaming history, things have gone well of late. If these trends continue and the increased sponsorship money is invested in the right areas then there is no reason why 2019 won’t be another historic year for esports.
The 4 Main Security Threats to the Corporate Database
With every passing year, cybersecurity attacks seem to be getting more brazen, intense and damaging. From enormous botnets that bring down the most popular websites in the world to government-sponsored hackers that seek to influence the result of an election in a rival country.
The danger of cyber attacks is further compounded by the rise of the Internet of Things (IoT). From the couple of billion devices connected to the Internet today, experts project at least tens of billions of gadgets will be plugged into the IoT within the next decade.
While there are numerous potential targets of a cyber attack, most hackers will focus on penetrating corporate databases. And with good reason—this is the place they are likely to get the highest payoff if their attack is successful.
The database contains the most sensitive information such as customer details, transaction histories, employee records, company financials, intellectual property, and corporate secrets. Keeping your company’s database secure is therefore vital. It all begins with knowing what the biggest threats are.
1.Poor Password Management
User IDs and passwords are the first and main barrier to an unauthorized person gaining access into your databases. Ergo, if your passwords aren’t strong enough or secured enough, you risk giving unfettered front door entry into your database. Though the average adult now knows what good password management involves, a surprising number of users and organizations have low standards for password protection.
A good password should have a mix of lower case letters, upper case letters, numbers, and special characters. A password should expire after 3 to 6 months and when it does, shouldn’t be reused for at least one year. Passwords should never be written down.
2.Unnecessary User Privileges
Database users should have rights assigned to them based on the principle of least privilege. Unfortunately, it isn’t unusual for system administrators to grant employees or third parties more privileges than they need to perform their work. Sometimes these are privileges that were meant to last for just a couple of weeks as part of a project role the user had been assigned but administrators subsequently forgot to revoke them.
Excessive privileges may be abused by the user. A hacker would also have more power than they otherwise would have if they were to hijack the account. System and database administrators should work closely with the human resources department to ensure user rights are consistent with the least privilege principle and that they only have the privileges they need. Regularly conduct a database audit to confirm that each user’s current privileges are required.
3.Inadequate Data Segregation
Your database likely contains a wide range of data of varying degrees of importance and sensitivity. Therefore, you cannot treat all the information in the database the exact same way. Data that is highly sensitive should receive a higher degree of protection.
You should classify all the data into different levels of sensitivity, then limit access to the most sensitive information to only a small group of authorized persons. You should be especially careful with the information third-party contractors can see when you give them temporary system access. Overall, no user should see data that they don’t need.
4.Absent or Inconsistent Patching
Each year, hundreds of database vulnerabilities are discovered. To seal these loopholes, software development companies will regularly release updates. If you do not apply these patches to your database and servers when they are released, you leave your systems vulnerable to a wide range of known weaknesses.
Remember, the average hacker usually doesn’t have the time to discover new loopholes. They’ll instead find out what database version you are running then search the web for the vulnerabilities associated with that version. They’ll subsequently seek to exploit these proven vulnerabilities. If your database doesn’t have the latest patches applied, you are at greater risk of attack and exploitation.
These are the main reasons databases become insecure. Others include poor audit trail monitoring, inadequate backups, unencrypted data, and human error. Understanding these weak points is vital in ensuring your database is secure and stable at all times.
Image; DepositPhotos
How to win a PS4 Pro or Xbox One X? Open the mystery box on DrakeMall!
Does the avid gamer inside you crave to get his hands on the new Sony PlayStation 4 Pro and Xbox One X consoles? Do you have to suppress your wish due to the steep price tag of these two ultimate consoles? Well! You are not alone. Most of the gamers out there have to do the same due to budget constraints. What if we tell you that you can win a PS4 Pro or get Xbox One X for almost free? No! We are not talking about any contest here but of the mystery box website of DrakeMall. Drake Mall is an e-commerce website that works on the ‘Spin-to-Win’ principle and provides you with a chance to win a PS4 Pro or Xbox One X in Gamer Case for a mere $35.99.
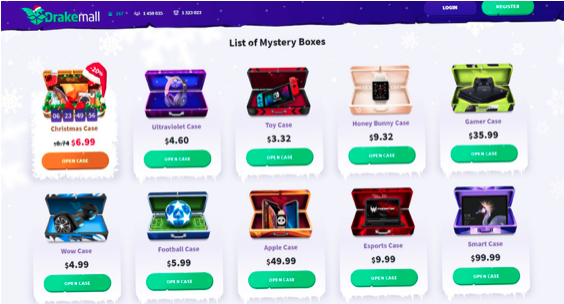
Just like the Gamer Case, DrakeMall holds various other virtual cases or mystery boxes with each case representing a particular category of products. Same way as the wheel of fortune in a casino, you have to try your luck in DrakeMall by spinning your way for the products present in the bought virtual case. The cool thing is that you will definitely win a product and never have to go empty-handed. Now, decidedly, you might have a lot of questions in your mind regarding the working of the mystery brand of Drake Mall. Continue reading ahead as we attempt to answer most of your questions in this post.
Win a cheap new PS4 or an Xbox One X on DrakeMall – Where to start?
Your first step is to register yourself and create an account on the website of DrakeMall. You can log in with your Google+, Facebook, or Twitter Account as well. The user interface of this mystery brand known as DrakeMall.com is charming enough to enchant your senses with the sheer number of mystery boxes or virtual cases present on the website. However, your concentration must be on the Gamer Case which comes with a price tag of $35.99. Simply click on the case to check its contents. You will notice a ‘Test Spin’ button here. You can click it for as many times as you want until you feel you are ready to grab in the real opportunity and acquire the experience of playing your favorite games like Red Dead Redemption 2, Spider-Man PS4 etc. on your dream gaming console.

However, before you start, you require adding funds to your DrakeMall wallet. All standard methods of payment including PayPal and even Drake Mall gift cards are accepted. Once you are done with the test spins, tap on ‘Open Case’ to buy the gaming mystery box and garner a finite number of spins. You can start with the actual spinning now.
What can you do with the products that you win on DrakeMall?
If you are lucky and one of your spins stop on the PS4 Pro or Xbox One X then you can simply request for delivery of the same at your location through the ‘Products’ section present under your profile. The beauty about DrakeMall is that the website delivers to every nook and cranny of the world where a post office is present. However, please note that you have to bear the customs duty yourself and depending upon the product, the website levies a delivery fee of 5 to 20 credits.
Please note that DrakeMall has totally customer-friendly policies. So, there is no need to dishearten yourself in case you didn’t win the dream gaming consoles. The website provides you the facility of exchanging the item you won with an item of same value or else you can sell the item you won to acquire Drake Mall credits. You can utilize these credits to try your luck again in different cases.
Final Words – Fulfil Your Dreams on Drake Mall
If you fear about the legitimacy of DrakeMall, please don’t worry at all. DrakeMall has got several user opinions, reviews, and unboxing videos available online. Besides this, the website operates under the Curacao E-Gaming License. DrakeMall has got complete potential to fulfill your dream of losing yourself in the cool gaming world of Xbox Live and Play Station Network (PSN). When you are on DrakeMall, don’t forget to check our other mystery boxes like the Apple Case or Esports Case!