Parkinson’s disease (PD) is a progressive neurological condition that affects the nervous system. And while one of the main symptoms of the disease is tremors, there are several others that cause just as many issues. One of the most common complaints about PD patients is constipation. And while there are some new and innovative options in which to solve this problem, scientists aren’t convinced they’re ready to be used yet.
The main treatment in question is called Fecal microbiome transplantation (FMT). Another is the use of pre- and probiotics in order to restore a healthy microbial balance in the gut.
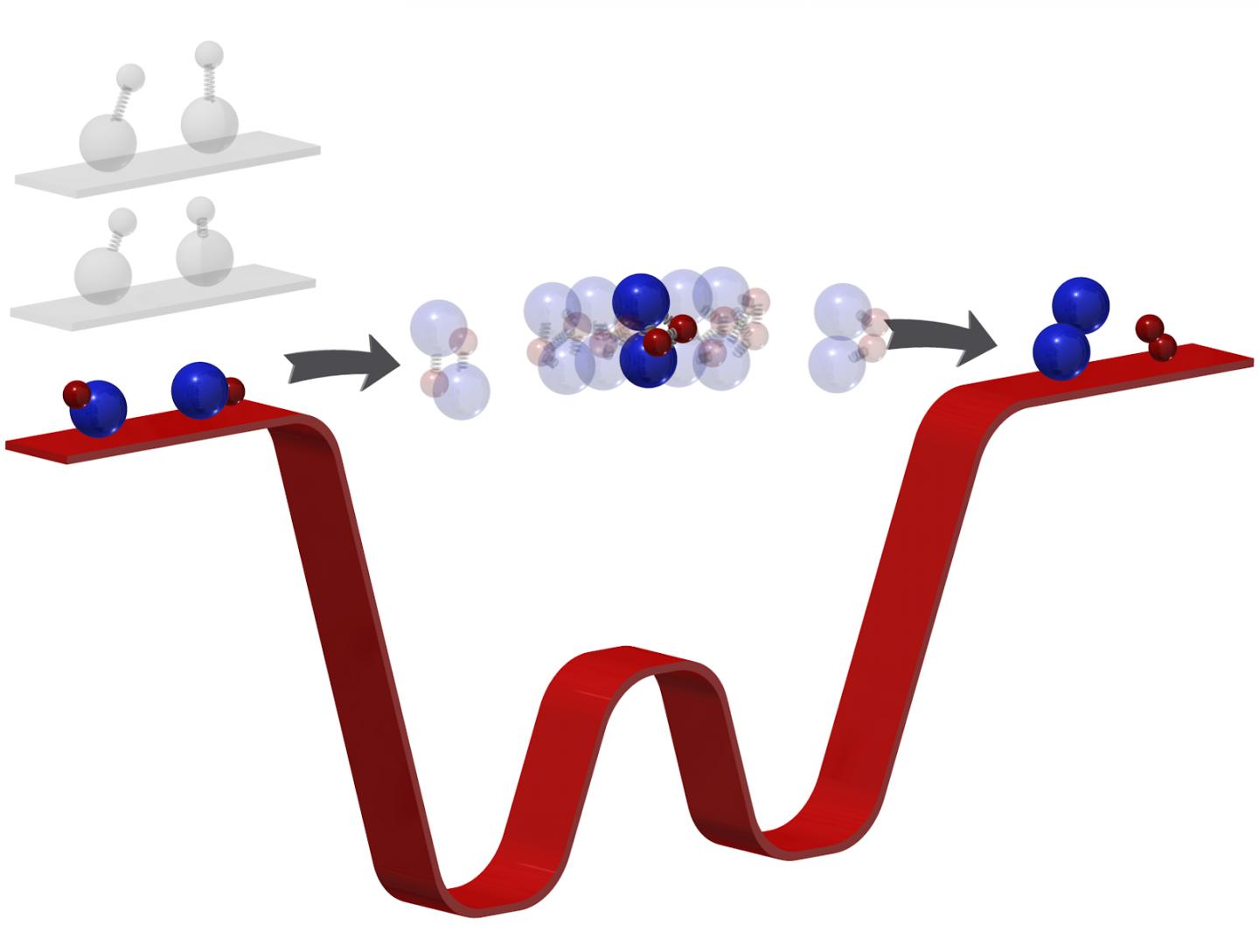
FMT involves the transporting of liquid filtrate feces from that of a healthy individual to a PD patient via a nasoduodenal or nasogastric tube, colonoscope, or enema.
“FMT is an interesting option for restoring the changes in the microbiome of PD patients,” says lead investigator on the study, Tues Van Laar, MD, Ph.D., Director of the Parkinson Expertise Center Groningen, Department of Neurology, University Medical Center Groningen, The Netherlands. “It is an attractive technique because the administration is relatively simple and in general it has only a mild pattern of adverse effects.” The problem is that as of yet, no rigorous clinical trials have been conducted, leaving many unanswered questions about the whole FMT treatment process.
In regards to the pre- and probiotics, Lactobacillus and Bifidobacterium administered over a 4-12 week period, has been proven to effectively treat constipation in PD patients. However, there is no solid data available regarding the potential side effects of these treatments when give to those with PD.
Following successful prebiotic animal trials, the first human trial of FMT for PD patients is now in action at the University of Ghent in Belgium and is scheduled to be finished by the end of 2019. The trial consists of 40 PD patients, each of whom will receive follow up assessments quarterly. During these meetings, the patient’s PD symptoms will be assessed to see what improvement, if any, has been made.
The investigators believe that there needs to be more clinical data available before allowing PD patients to undergo FMT treatment. There are various knowledge gaps that need to be filled first, including the optimal route of administration of FMT, the frequency or content of FMT, and what possible adverse side effects could occur as a result of FMT.
“FMT is a black box with too many unanswered questions at the moment, also with respect to safety concerns,” advises Prof. van Laar. “FMT or the use of pro- and prebiotics might become standard treatments in selected subgroups of PD patients in the future, but there are no good data yet in the public domain to support their use in PD patients.” The team is hopeful that this review will spur others on to begin more in-depth research into this topic as opposed to starting the therapy without any solid clinical data.