There are already more than 8 billion devices dotted around the world, all connected to what we call the “internet of things”. This includes vehicles, medical devices, wearables, and all other kinds of smart technologies. It’s estimated that by 2020, more than 20 billion devices will be connected together, all sharing and uploading data online.
The problem is that those devices are all very vulnerable to hackers who can jam signals, overwrite data, and just generally, be a nuisance. One way people can protect their data is through a method known as “frequency hopping.” Frequency hopping is the process of sending each data packet via a unique radio frequency (RF) channel so that no individual packet can be pinned down. And while frequency hopping is good, hopping large packets still take too long and those with fast hacking skills are still getting in.
To combat this issue MIT researchers have now developed a new kind of hopping transmitter that’s quick enough to stop even the fastest of hackers. The way it works is by leveraging frequency-agile devices known as bulk acoustic wave (BAW) resonators to quickly flip between different RF channels sending bits of information each time. As well as those researchers built in a channel generator that randomly selected a different channel to send a bit to every microsecond. They also developed a wireless protocol in which to facilitate the fast frequency hopping.
“With the current existing [transmitter] architecture, you wouldn’t be able to hop data bits at that speed with low power,” explains Rabia Tugce Yazicigil, a postdoc in the Department of Electrical Engineering and Computer Science and first author on the paper. “By developing this protocol and radio frequency architecture together, we offer physical-layer security for connectivity of everything. More seriously, perhaps, the transmitter could help secure medical devices, such as insulin pumps and pacemakers, that could be attacked if a hacker wants to harm someone.”
One way in which hackers attack wireless devices is through a process called selective jamming. This is where a hacker manages to intercept and corrupt data packets being transmitted from a single device yet leave all others untouched. These attacks are often hard to detect and are sometimes mistaken for poor wireless links. For that reason, they’re hard to catch with existing frequency hopping transmitters.
With frequency hopping, data is sent across various channels based on a sequence that’s been predetermined with the receiver. Packet-level frequency hopping works slightly different in that it sends one data packet at a time across a range of 80 channels, on a just a sole 1-megahertz channel. The whole process takes around 612 microseconds to complete, and the problem is that hackers can locate the channel in the first microsecond and send a command to jam the packet.
“Because the packet stays in the channel for a long time, and the attacker only needs a microsecond to identify the frequency, the attacker has enough time to overwrite the data in the remainder of the packet,” says Yazicigil.
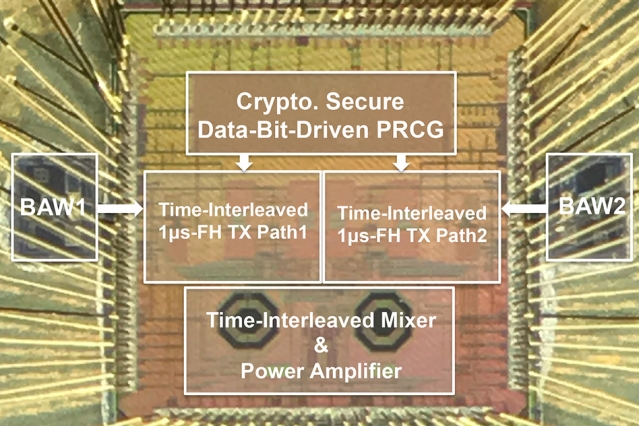
In order to build their ultrafast frequency-hopping method, the researchers had to replace the crystal oscillator with one that was based on a BAW resonator. The problem with that is BAW resonators fall short of the 80-megahertz that’s available for wireless communication in the 2.4-gigahertz band, and can only cover a range of around 4 or 5 megahertz of frequency channels.
To get around that issue, they incorporated components that split the input frequency into several different frequencies. Then a mixer combines these divided frequencies with the BAW frequencies to get a whole new host of radio frequencies capable of spanning around 80 channels. The next step involved randomizing the way in which data was sent. To do this the researchers used a system where each microsecond generated a pair of separate channels.
Loaded with a secret key that’s pre-shared with the transmitter, the receiver gets to work navigating a 1 bit down one channel and a 0 bit down the other. However, the channel carrying the desired bit is always going to be the one that’s displaying more energy. When the receiver compares the two channel’s energies it takes note of which one is higher and proceeds to decide the bit sent on that channel. The channel selection is both fast and random. And, because there’s no fixed frequency offset, there’s no way to tell which bit is going down which channel making selective jamming no better than a random guess.
The team’s final innovation involved the integration of two transmitter paths into a more efficient form of architecture. In doing so, they enabled the transmitter to receive the next selected channel while still sending data on the existing channel. The workload then alternates. This ensures there’s a 1-microsecond frequency-hop rate and also preserves the same 1-megabyte-per-second data rate that applies to most BLE-type transmitters.
More News to Read
- Researchers Gain Deeper Understanding into Quantum Technology Thanks to Superconducting Vortex
- MIT Researchers Create New Way of Enhancing Light and Matter Interactions
- New Fuel Reducing Ship Coating Could Save the U.S. Navy Millions of Dollars
- New NASA Mission to Focus on Interstellar Space Particles of the Outer Solar System
- AI is Now More Accurate at Diagnosing Skin Cancer than Dermatologists

